Deep Dependency Scanning
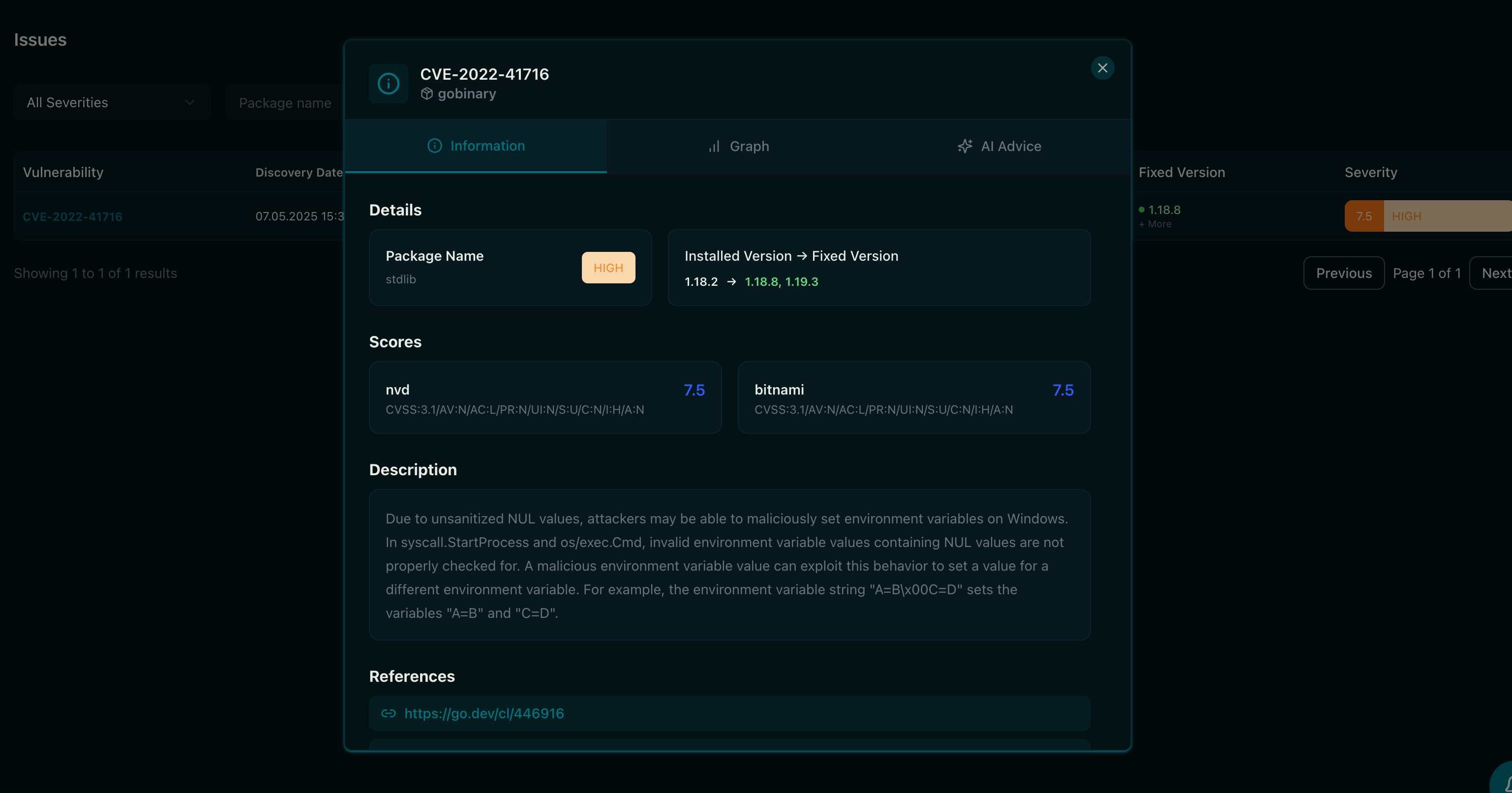
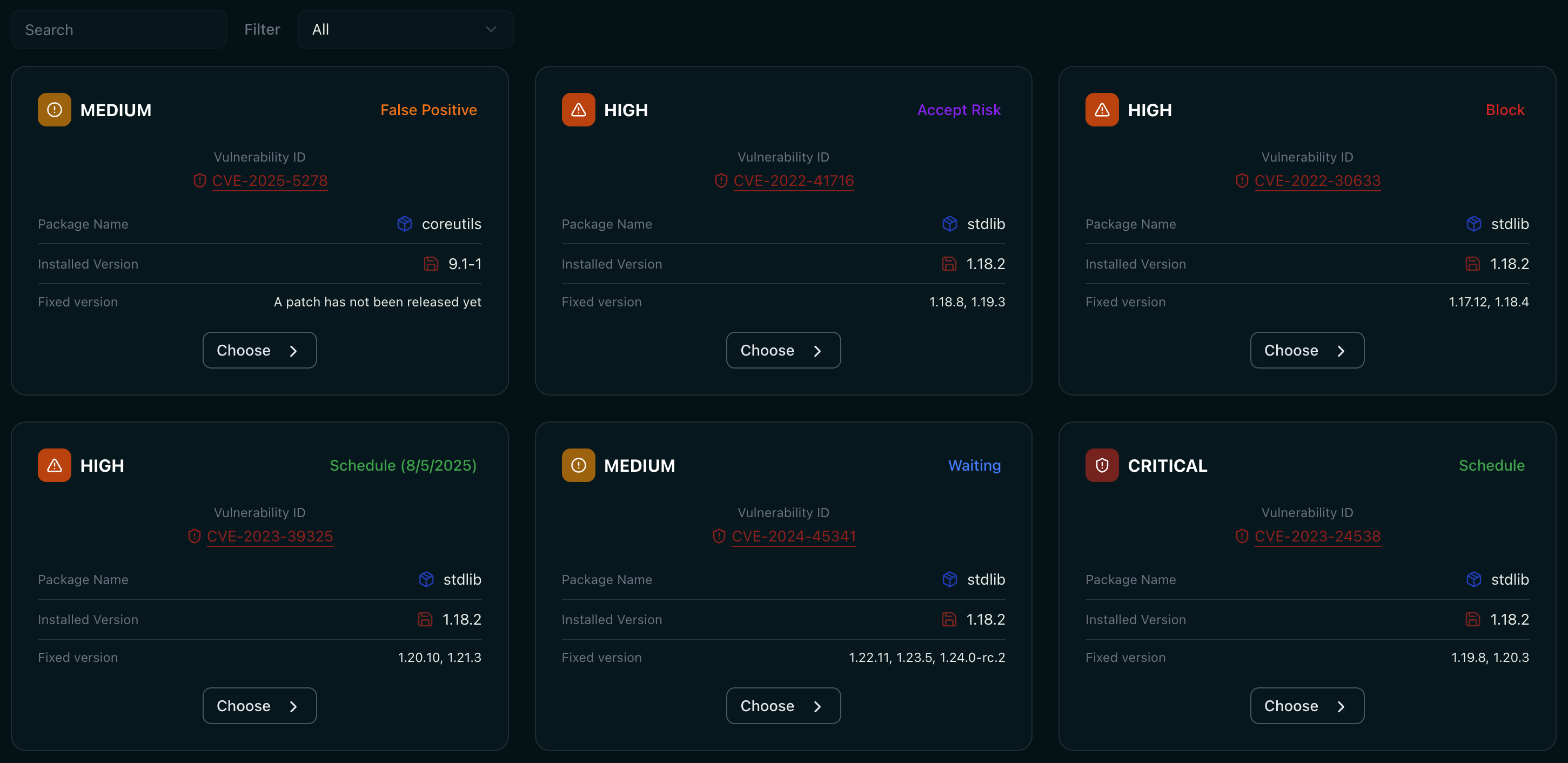
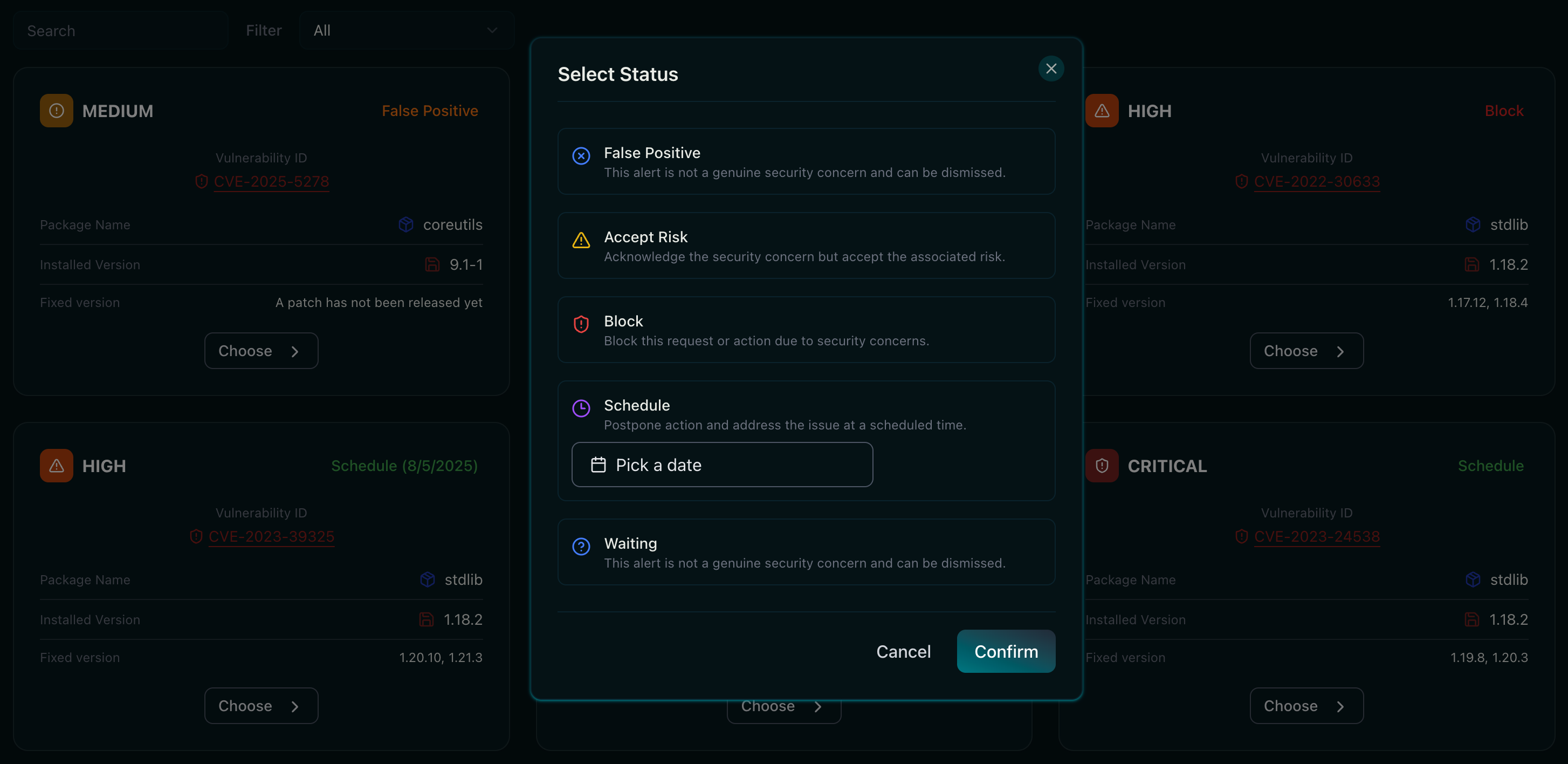
Scans all direct and transitive dependencies across multiple programming languages, providing complete visibility into your software stack and ensuring vulnerabilities are detected and addressed throughout every layer of your projects.